Key management by the Commvault software includes the ability to generate random encryption keys for the stored data and also manage the secure storage of these keys.
Key Generation
The software uses the CTR_DRBG random number generator to generate the encryption keys. The software also uses various random OS-supplied data to provide a dynamic seed for the random number generator. The software generates the keys as follows:
-
Random 128-bit or 256-bit data encryption keys (DEK) for every client and storage policy copy combination, and initial vectors (IV) for CBC chaining during data encryption.
-
Random 128-bit or 256-bit master key for the storage policy copy in absence of third party key management server
The software uses the AES Key Wrap Specification to securely encrypt the encryption keys and store the encrypted keys in the CommServe database with CRC32 embedded. The software uses CRC32 only to check whether a key is entered incorrectly. If the software detects an error, you will receive a prompt to check for network/media malfunction.
Key Lifecycle
Key management for different types of encryption works as follows:
-
For Hardware Encryption:
-
Commvault generates a different random 128 or 256 key for every data chunk it writes. Each job can contain multiple chunk, so each backup job can have multiple randomly generated keys. With multiple different keys the strength of the encryption is very high.
-
Key is encrypted and stored in the CommServe database.
-
When data chunks are pruned (erased), the database entry and the associated key for that data chunk is deleted. Open keys in memory are deleted using memset().
-
-
The Commvault manages software encryption as follows:
-
The software generates a master key for each storage policy copy.
If a third party Key Management Server (KMS) like SafeNet is enabled, then the software obtains the master key from the KMS.
The software generates a key encryption key (KEK) RSA public-private key pair with length of 3072 bits for each storage policy copy.
The software uses a master key to encrypt the private portion of KEK.
The software uses the default key to encrypt the public portion of KEK.
-
The software encrypts the RSA public-private key pair and the master key, and stores the encrypted key pair and master key in the CommServe database.
If you use a third party KMS, then the software stores only the key ID in the CommServe Database.
-
-
The software generates a new key for each client and storage policy copy combination. The software uses the public key of the storage policy copy to encrypt the keys and stores the encrypted keys in the CommServe database.
-
When jobs are pruned (erased), the software deletes the database entry and the associated key for that job. The software uses memset() to delete the open keys in memory.
-
For the jobs on which deduplication is enabled, the software removes the keys when the store is sealed and all jobs get pruned.
-
You can optionally store the encryption keys on the backup media by selecting the Via Media Password option in the properties dialog box of a storage pool or a storage policy. If you lose the job history from the CommServe database for various reasons like manual deletion of entities, aged data or loss of the entire CommServe database, you can catalog and import job history using external tools.
Notes:
-
To perform restore and auxiliary copy operations using the CommCell Console, the software automatically provides the specific key for each data chunk / client and storage policy copy combination. (Data chunks for hardware encryption, and client and storage policy copy combination for software encryption.)
-
To perform the restore operations using the Media Explorer, the software provides an option in the data path to store the encryption key on the media.
-
To perform disaster recovery, the software backs up the keys regularly during scheduled export and backup of the CommServe database (DR Backup task).
Data Flow for Key Management Operations
Storage Pool Creation
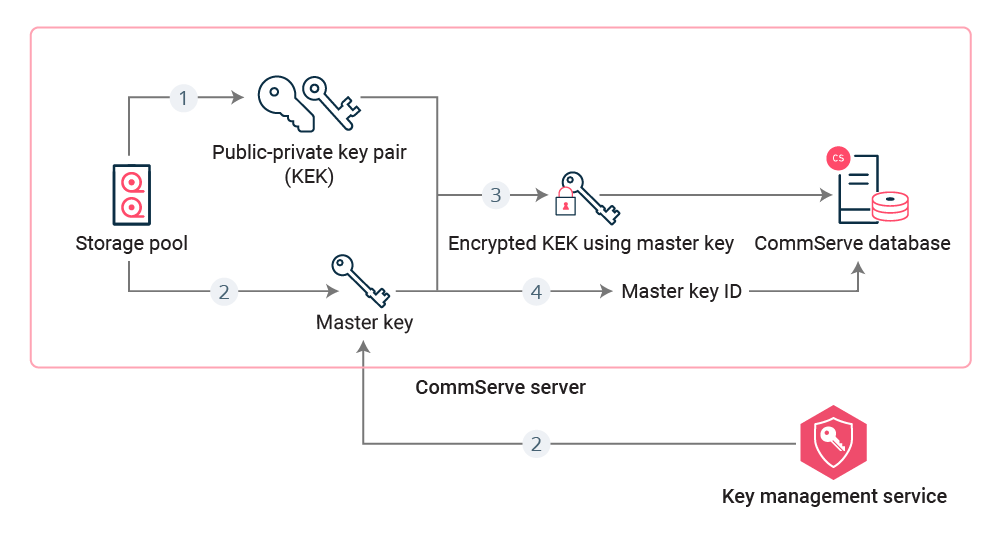
-
Software generates KEK (Public-Private) for the storage pool.
-
Software sends request to the KMS to generate master key, and then the KMS generates master key.
-
Software encrypts private portion of KEK using master key, and then stores encrypted KEK in the CommServe database.
-
Software stores master key ID in the CommServe database. (For built-in KMS, scrambled master key is also stored in the CommServe database).
Backup
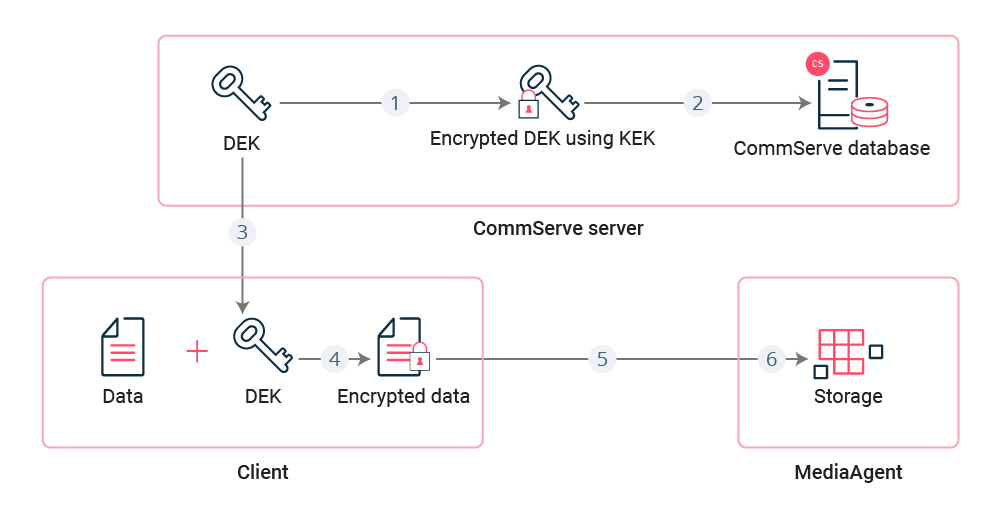
-
Software generates data encryption key (DEK) for the client.
-
Software encrypts DEK using public portion of KEK, and then stores encrypted DEK in the CommServe database.
-
CommServe sends DEK to the client. The software protects DEK over the network using client network password.
-
Client encrypts backup data using DEK.
-
Client sends encrypted data to the MediaAgent.
-
The MediaAgent writes encrypted data to the target backup storage.
Restore
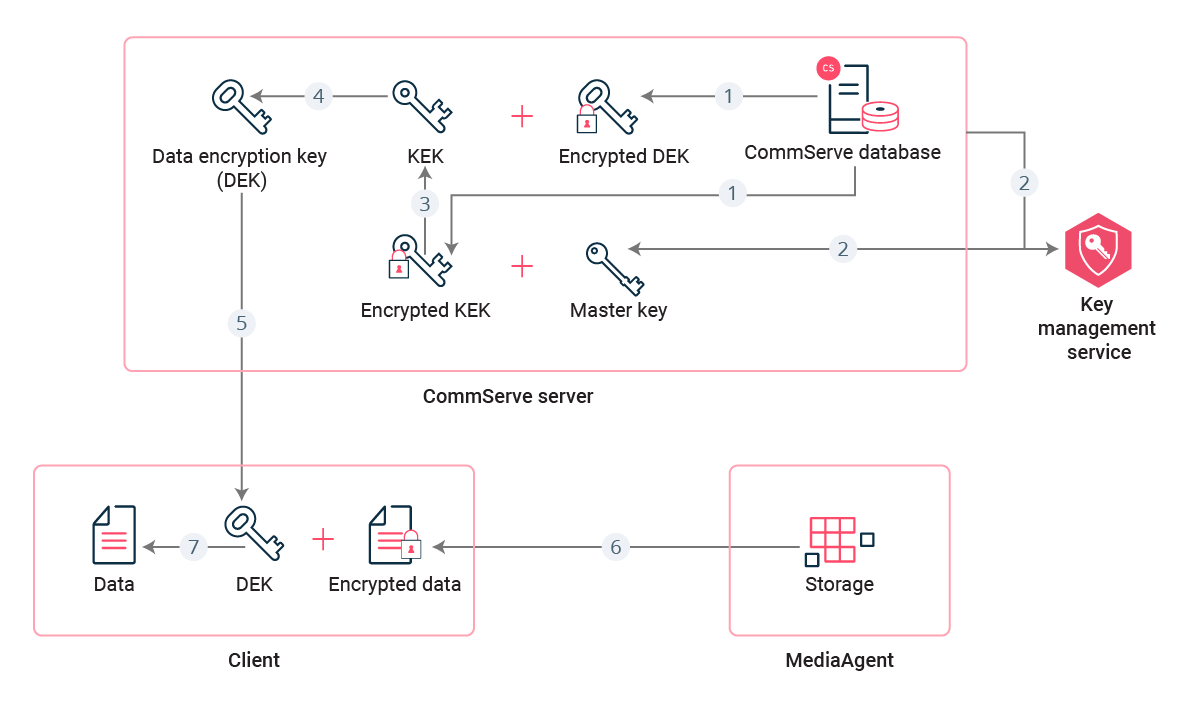
-
The CommServe server fetches the encrypted Private portion of KEK and the encrypted DEK from the CommServe database.
-
The CommServe server fetches the master key from KMS.
-
The CommServe server decrypts Private KEK using master key.
-
The CommServe server decrypts DEK using Private KEK.
-
The CommServe server sends DEK to client. The software protects DEK over the network using client network password.
-
The MediaAgent sends encrypted data to the client.
-
The client decrypts data using DEK.