To integrate with Azure AD, add a SAML application in your Azure AD account and in the Command Center. Metadata from the Azure application (IdP) and the Command Center application (SP) are shared during this process.
Azure Active Directory is a third-party identity provider (IdP) that can act as the IdP when your users log on to Commvault. Commvault is the service provider (SP).
Considerations
Microsoft supports up to 150 user groups for each SAML token. If a user belongs to more than 150 user groups when Azure AD issues the SAML token, they may experience unpredictable results. For more information about configuring group membership in tokens to prevent this issue, see the Microsoft documentation website.
Before You Begin
-
You must have the Azure Active Directory Premium P1 or Premium P2 edition. For information, go to the Azure Active Directory documentation.
-
If you need to create a SAML app for a specific company, in the upper-right corner of the page, from the Select a company list, select the company that you want to create the SAML app for.
-
Verify that groups in Azure AD have the exact name as the Commvault user groups you want to map them to. If an Azure AD group does not have the exact name as the group you want to map it to in Commvault, complete one of the following:
-
Create a new user group in Commvault that has the exact name as the group in Azure AD.
-
Rename the Azure AD group to match the user group in Commvault.
-
Create an Application in the Azure Portal
-
Go to the Azure portal.
-
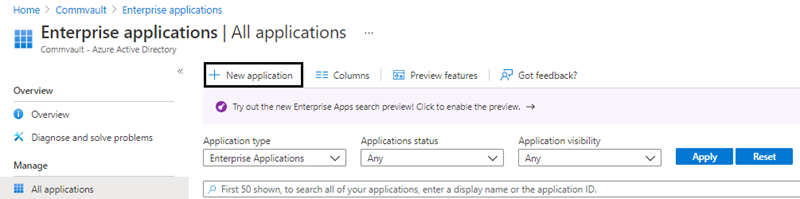
From the navigation pane, go to Azure Active Directory > Enterprise applications, and then click New application (
 ).
).
-
Under Browse Azure AD Gallery, click Create your own application.
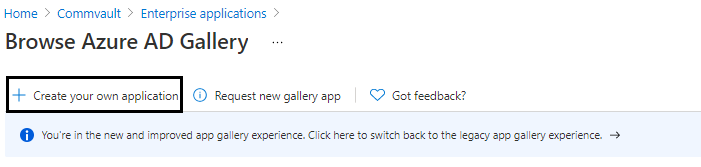
-
Enter a name for the application, select Integrate any other application you don't find in the gallery (Non-gallery), and then click Create.
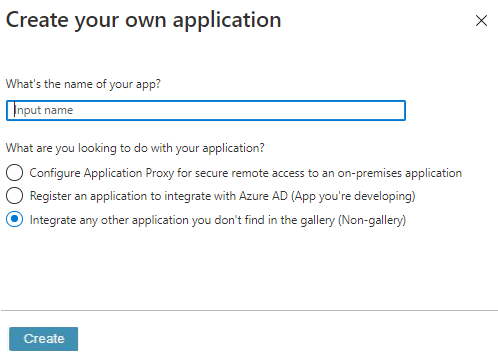
-
Review the overview, and under the Getting Started section, complete the following steps required by Microsoft: Assign users and groups and Add user/group.
Note
Only the users and groups that are assigned in the steps can access the application.
-
From the navigation pane, go to Single sign-on, and then click the SAML tile.
The SAML-based Sign-on page appears.
-
In the upper-right corner of the Basic SAML Configuration section, click Edit.
-
In the Identifier (Entity ID) box and the Reply URL (Assertion Consumer Service URL) box, enter the Web Console URL, and then click Save.
Enter the URL in the following format: https://hostname:443/identity. For example, if you use Commvault Cloud, enter https://mnnn.metallic.io:443/identity where nnn is your ring number.
-
In the upper-right corner of the User Attributes & Claims section, click Edit.
-
In the Unique User Identifier box, specify user.userprincipalname.
-
In the SAML Signing Certificate section, beside Federation Metadata XML, click Download.
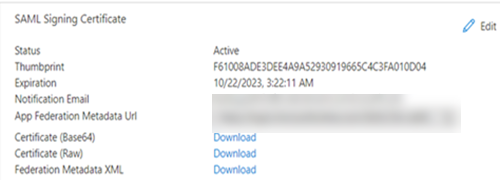
The federated metadata file that you download is the IdP metadata file that you will upload to Commvault.
-
Remain on the SAML-based Sign-on page.
You must upload the SP metadata file created in Commvault to your Azure application from the SAML-based Sign-on page.
Add a SAML Application in Commvault
-
From the navigation pane, go to Manage > Security.
The Security page appears.
-
Click the Identity servers tile.
The Identity servers page appears.
-
In the upper-right corner of the page, click Add > SAML.
The Add SAML app page appears.
-
On the General tab, in the Name box, enter the domain name that you want to associate users with.
Note
-
The SAML application is created using the domain name.
-
For SAML user groups mapping to function correctly, the name that you enter here must be the same as your Commvault Cloud Tenant Name.
-
-
Click Next.
-
On the Identity provider metadata tab, in the Upload IDP metadata box, browse to the XML file that contains the IdP metadata, and then click Open.
The Entity ID and the Redirect URL from the file are displayed.
-
Click Next.
-
On the Service provider metadata tab, review the value in the Service provider endpoint box.
This value is automatically generated and is used in the SP metadata file. The format of the value is https://mycompany:443/identity.
-
To digitally sign the SAML message, move the Auto generate key for digital signing of SAML messages toggle key to the right.
-
Click Next.
-
On the Associations tab, identify the users who can log on using SAML:
-
To identify users by their email addresses, in the Email suffixes box enter an email suffix, and then click Add.
Note
You must use an email suffix as specified in the SAML integration settings to avoid integration issues.
If you face SAML integration issues, use a break glass account. The break glass account must be on different domain than that of the current domain.
-
To identify users by the companies they are associated with, from the Companies list, select a company, and then click Add.
-
To identify users by the domains they are associated with, from the Domains list, select a domain, and then click Add.
-
To identify users by the user groups they are in, from the User groups list, select a user group, and then click Add.
Note
-
If you migrate from an Exchange On-premises server to an Exchange Online server, you must add the appropriate domain and user group.
-
You can add any combination of associations, and you can add multiple associations in each category.
-
-
-
Click Next.
The Connectivity Test screen appears.
-
To add the SAML app in the IdP and test the connection:
Note
You can skip this step and click Finish to add the SAML app in the IdP, later. Further, you can test the connection on the SAML app page in the General section.
-
On the Connectivity Test screen copy the (Single Sign-On) SSO URL or download the SP metadata.
-
In a separate browser window:
-
Using the SSO URL and the SP metadata, create a SAML app in the IdP website.
-
In the SAML app that is created in the IdP, update the SSO URL or upload the SP metadata.
Note
Some IdPs such as OKTA require you to update the SSO URL, while other IdPs such as Azure require you to upload the SP metadata.
-
Sign out of any existing IdP sessions in your browser window.
-
-
On the Connectivity Test screen:
-
Click Test login.
A browser window appears.
-
Enter the email and password for a user to test the SAML login.
-
Close the browser window.
After the test login is successful, the SAML app will be enabled in the Command Center.
-
-
-
Click Finish.
The SAML app screen appears.
-
On the General tab, in the General section, next to the NameID attribute, click the Edit button
 .
. -
From the NameID attribute list, based on the attributes in the IdP response, select either Email or User Principal Name.
-
Click Submit.
The SP metadata file must be uploaded to the Azure application.
Upload the Metadata to the Azure Portal
-
In the Azure portal, on the Single sign-on page, click Upload metadata file.
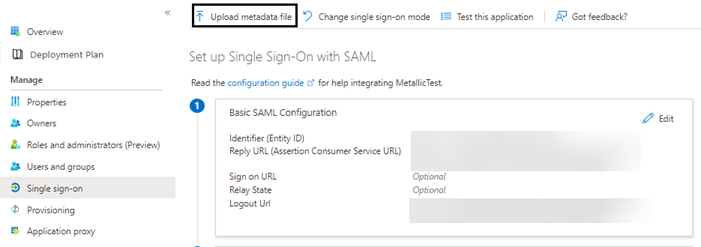
-
Upload the SP metadata file.
-
Click Add.
The Identifier (Entity ID), Reply URL (Assertion Consumer Service URL), and Logout URL values are pre-filled using the SP metadata file.
-
Click Save.
Optional Azure Configurations
Configure SCIM for Synchronization
-
To synchronize the Azure application with Commvault software on regular time interval, go to Azure portal.
-
Under Azure services, click Enterprise applications, and then click the application name.
-
From the navigation pane, go to Provisioning > Get started.
The Provisioning page appears.
-
Under Provisioning mode, select Automatic from the drop-down list.
-
Under Admin Credentials, provide the Tenant URL and the Secret Token.
Note
-
In Command Center, copy the Provisioning URL (Tenant URL) that is available under the Service provider metadata tab of the SAML application created for SCIM synchronization.
-
The secret token can be created or fetched from the Access token tab under the user that is configured for SCIM synchronization.
-
-
Click Test Connection.
On the top-right screen, the test connection success message appears.
-
Click Save.
-
Under Mappings, perform the following operations:
-
To modify the mapping for the user groups, click Provision Azure Active Directory Groups.
-
Under Target Object Action, uncheck Delete option.
The SCIM provisioning can only allow to modify user group membership.
-
Under Attribute Mappings, for displayName, modify the matching precedence value as 2 and for objectId, modify the value as 1.
Note
-
Save the Attribute mapping after modifying precedence value for displayName and then, modify the value for objectId.
-
If a user is manually removed from the Commvault user group, the next synchronization will not include that user to the user group.
-
-
Click Save.
-
-
To modify the mapping for the users, click Provision Azure Active Directory Users.
-
Under Target Object Actions, uncheck Create option.
The SCIM provisioning can only modify the user properties, and delete the users.
-
Under Attribute Mappings, delete the attributes except userPrincipalName, Switch, displayName, mail, and givenName.
-
To add objectId attribute to the list, click Add New Mapping.
-
Under Source attribute, select objectId.
-
Under Target attribute, select externalId, and then click Ok.
-
Click Save.
-
-
Under Settings, to apply the SCIM provisioning for all the users of the Azure environment, from Scope, select Sync all users and groups.
-
Under Provisioning Status, click On.
-
Click Save.