You can protect the Commvault software encryption keys with third-party key management server before storing the keys in the CommServe database. The software encryption keys are required to perform restore and auxiliary copy operations.
Supported Key Management Servers
-
Key Management Interoperability Protocol (KMIP) key management server products of any version:
-
Note
- To use a KMIP key management server other than the products listed above, contact your software provider.
- The certificate used must not be encrypted
Data Flow for Key Management Operations
Storage Pool Creation

-
Software generates KEK for the storage pool.
-
Software sends request to the KMS to generate master key, and then the KMS generates master key.
-
KMS encrypts KEK using master key, and then sends encrypted KEK and master key ID to the software.
-
Software stores master key ID and encrypted KEK in the CommServe database. (For built-in KMS, scrambled master key is also stored in the CommServe database).
Backup
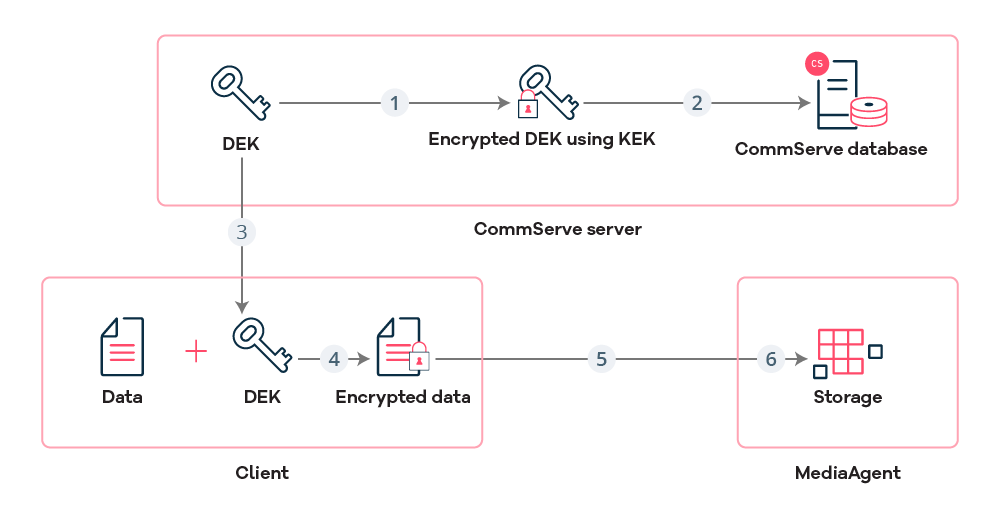
-
Software generates data encryption key (DEK) for the client.
-
Software encrypts DEK using KEK, and then stores encrypted DEK in the CommServe database.
-
CommServe sends DEK to the client. The software protects DEK over the network using client network password.
-
Client encrypts backup data using DEK.
-
Client sends encrypted data to the MediaAgent.
-
The MediaAgent writes encrypted data to the target backup storage.
Restore
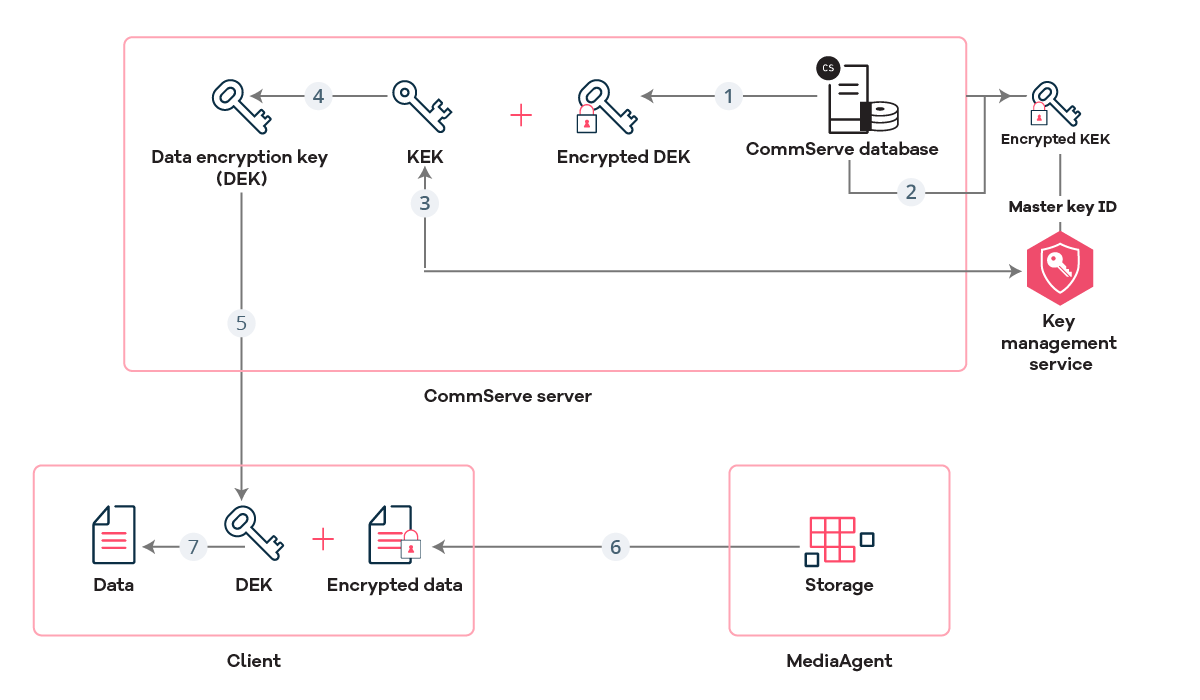
-
The CommServe server fetches the encrypted KEK and the encrypted DEK from the CommServe database.
-
The CommServe server fetches the master key from KMS.
-
The CommServe server decrypts KEK using master key.
-
The CommServe server decrypts DEK using KEK.
-
The CommServe server sends DEK to client. The software protects DEK over the network using client network password.
-
The MediaAgent sends encrypted data to the client.
-
The client decrypts data using DEK.
Related Task
Configuring Encryption Key Management using Third-party Key Management Server