The Acante Data Protection Readiness Report is a combined indicator of the impact and likelihood of breach for a specific dataset. Acante computes this risk score for each dataset (a table, such as MS SQL store, data warehouse, etc.), a collection (document store), a prefix (object store), and so on, depending on the type of datastore.
By identifying risky datasets, Acante helps data owners prioritize which data to focus on to reduce their overall data risk. The Acante data risk is a function of multiple attributes that capture both the likelihood of breach and the impact of that data being breached. These attributes include:
-
Sensitivity of data: This is based on the data classes (PCI, PII, PHI, etc.) and their associated sensitivity levels. This indicates the impact of the breach of this dataset.
-
Security configuration posture of the data: This captures the security configuration of the data, usually configured at the level of the datastore or platform. Insecure configurations increase the likelihood of a breach.
-
Data access volumes: This attributes captures the count of human or machine identities and roles that access the data, and their data access volumes. Frequently accessed data has a higher likelihood of breach.
-
Data access privileges: This attribute captures the count of human or machine identities and roles with access privileges to the data, accounting for the allowed actions. Data that has wide-access privileges has a higher likelihood of breach.
Before You Begin
-
Download the Acante Security Connector workflow from the Commvault Store, and then deploy it. For more information, see the following:
Procedure
-
From the navigation pane, go to Reports > Data Protection Readiness.
The Data Protection Readiness report appears. The following is a sample report:
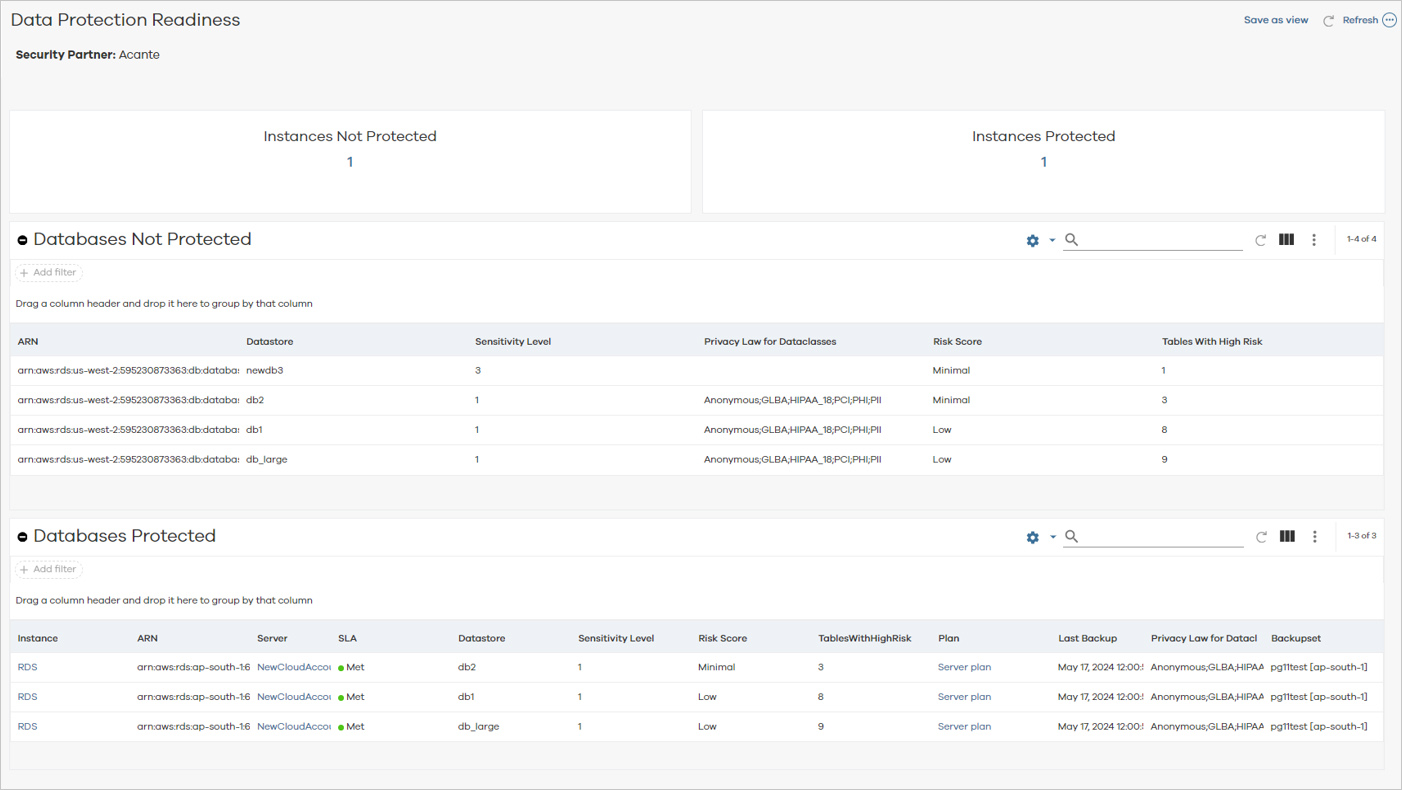
-
The following table entries in the report help define the overall risk of the data being examined by Acante:
-
Risk: The overall risk to your organization. The top two risk tiers (Extremely High and Elevated) require immediate attention. The other tiers (Moderate, Low, and Minimal), do not required immeidate attention, but should be evaluated and monitored.
-
Sensitivity: Sensitivity levels of data, defined as follows:
-
1 (Restricted): The most sensitive data in the organization, which poses significant risks if exposed. Access to this data should be restricted to the fewest possible list of users who need it for specific job functions. Typically, PHI or PCI data falls into this category.
-
2 (Confidential): This data is typically restricted to smaller teams in the organization. Exposure of this data could have significant impact to the orgnization and its reputation.
-
3 (Internal): This data is considered internal to the orgnization. While it may not pose a significant risk if exposed, it should be reasonably protected since there is some risk involved.
-
4 (Public): This data can be exposed and published to public external audiences.
-
-
Privacy Law for Dataclasses: Privacy laws applicable to the data (for example, HIPAA, PCI, PII, GDPR, PHI, and GLBA).
-