The File activity tab in the Threat Indicators dashboard lists Windows file system clients with backup job anomalies.
Clicking a client computer opens the File Activity Report, which allows you to analyze the statistics for that client.
File Activity Tab
The table in the File activity tab is comprised of the following columns:
|
Column |
Description |
|---|---|
|
Name |
The client computer. When you click the client computer, the File Activity Report appears (see below), which allows you to analyze the statistics for that client. |
|
Indicators |
The type of anomalous file activity, as follows:
|
|
Detected time |
The time when the anomaly was detected. |
|
Server type |
The type of server identified. |
|
Created files |
The number of files that were created at the detected time. |
|
Renamed files |
The number of files that were renamed at the detected time. |
|
Deleted files |
The number of files that were deleted at the detected time. |
|
Modified files |
The number of files that were modified at the detected time. |
|
Tags |
Audit tags that you can use to record actions. |
|
Actions |
Click the action button
|
File Activity Report
Click a client name in the table in the File Activity tab to open the File Activity Report for file system backup job anomalies.
The report is divided into the following sections: File Activity chart and Unusual File Activity table.
Note
To restore a client that has unusual file activity, click Recover files in the upper right corner of the File Activity Report. The system will restore the client to a state before the anomaly was discovered, ensuring a clean recovery. For more information, see Performing File System Restores.
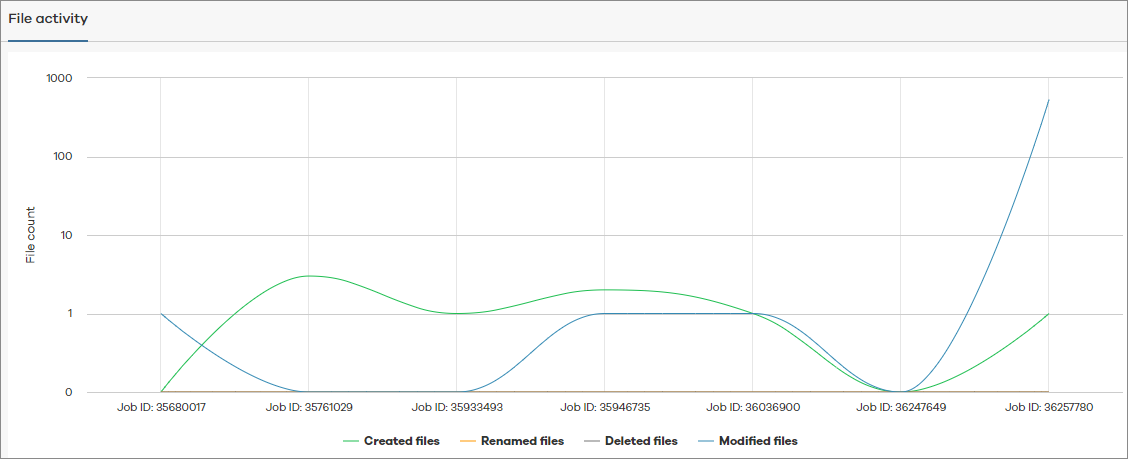
File Activity Chart
The File activity chart displays the distribution of the number of files in a backup job based on unusual behavior that is observed in creation, modification, and deletion operations.
Note
In the chart, System threshold serves as an indicator as to why jobs have been identified as anomalous. The system establishes the threshold by analyzing patterns from past backup jobs.
The following image is an example of the File activity chart for file system backup job anomalies:
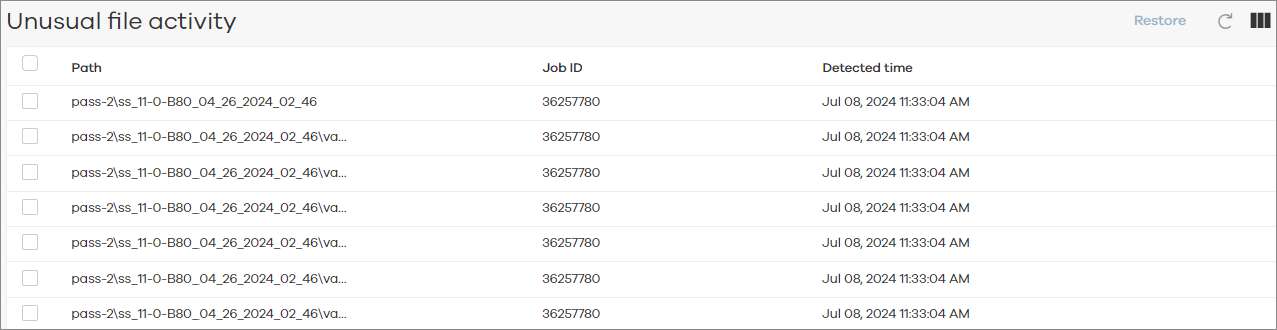
Unusual File Activity Table
The Unusual file activity table is comprised of detailed information about the affected backup job files in the client computer.
The following image is an example of the Unusual file activity table for file system backup job anomalies:
Note
To restore a path that has unusual file activity, select the checkbox of the path in the Unusual File Activity table, and then click Restore. The system will restore the path to a version before the anomaly was discovered, ensuring a clean recovery. For more information, see Performing File System Restores.
The following table includes descriptions for all columns in the Unusual file activity table for file system backup job anomalies.
|
Column |
Description |
|---|---|
|
Path |
The path to the folder that contains the files that are affected by the anomalous activity. |
|
Job ID |
The identifier of the backup job that has the anomaly. |
|
Detected time |
The time when the anomaly was detected. |
 , and then select one of the following options:
, and then select one of the following options: