The Threat Analysis Report summarizes the list of files containing anomalies on the latest backup jobs that have been file indexed. You can use this report to track different versions of a document to see if the file has been modified drastically. Modifications may occur if the file is encrypted or corrupted by malware attacks.
Note
Configure "File anomaly alert" with event code 69:52 to recieve alerts after every threat analysis job.
For more information about Threat Analysis, see Threat Analysis for File System.
Procedure
-
From the navigation pane in the Command Center, click Monitoring > Threat Indicators.
The Threat Indicators dashboard appears.
-
Click the Threat analysis tab.
A list appears, showing clients and subclients that contain infected files.
-
To view the report, click the name of the client or subclient for which you want to view the report.
The report appears.
Report Description
The Threat Analysis Report is divided into the following sections: Threat Analysis charts and File Information table.
Note
To remove the client that has unusual file activity from the client list, click Clear anomaly in the upper right corner of the Threat Analysis Report.
Threat Analysis Charts
The Threat Analysis charts display the infected files in the selected client for a specified time range.
The following images are examples of the threat analysis charts:
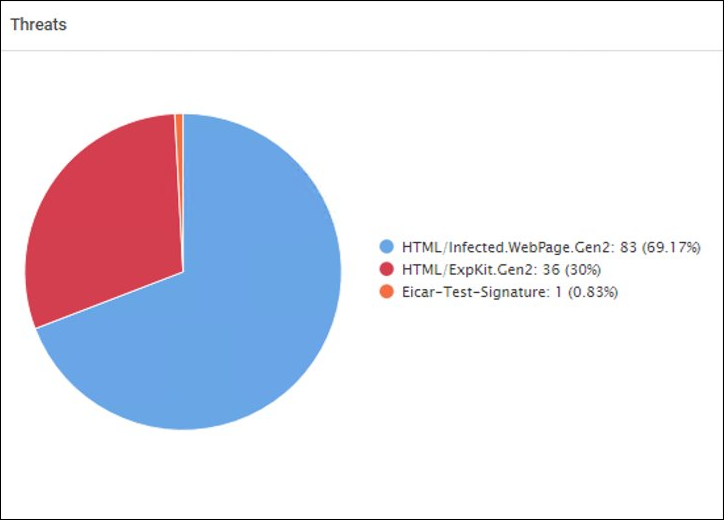
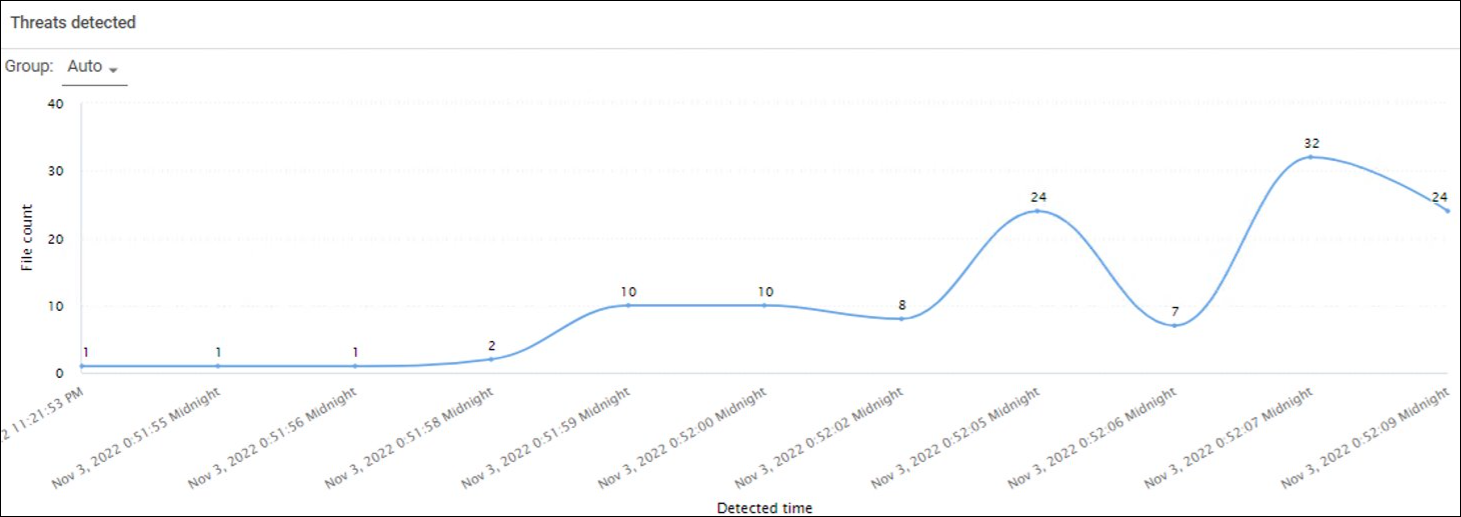
File Information Table
Click a recovery point in the Threats Detected chart to populate the File Information table.
The following image is an example of the File Information table:
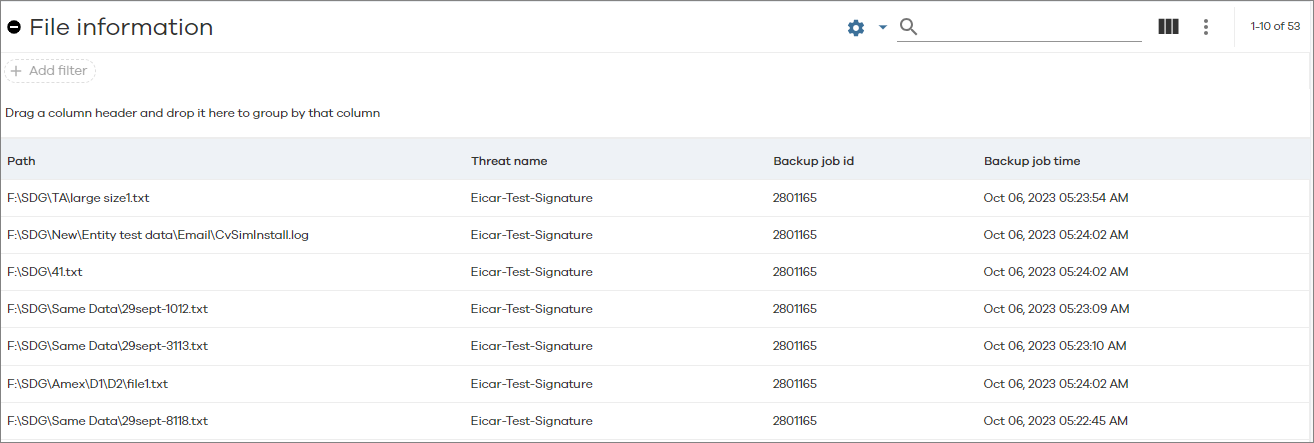
The following table includes descriptions for all the columns in the File Information table for Threat Analysis.
|
Column |
Description |
|---|---|
|
Path |
The path to the folder that contains the backed up file. |
|
Threat name |
The name of the threat, |
|
Backup job id |
The ID of the backup job that backed up that file, |
|
Backup job time |
The time at which the backup was performed, |