The Threat Scan Report summarizes the suspicious files found in a client, including those containing potential ransomware and/or malware infections.
For more information about Threat Scan, see Commvault Threat Scan.
Procedure
-
From the navigation pane in the Command Center, click Monitoring > Threat Indicators.
The Threat Indicators dashboard appears.
-
Click the Threat scan tab.
A list appears, showing clients that contain suspicious files.
-
To view the report, click the name of the client for which you want to view the report.
The report appears.
Report Description
The Threat Scan Report is divided into the following sections: Threat Scan tiles and charts, and Suspicious Files table.
Note
-
To recover files from a client that has unusual job activity, click Recover files. For more information, see Performing File System Restores.
-
To remove the client that has suspicious file activity from the client list, click Clear anomaly in the upper right corner of the Threat Scan Report.
Threat Scan Tiles and Charts
Threat Scan tiles and charts display statistics about suspicious files found on the client.
The following image is an example of the Threat Scan tiles and charts:
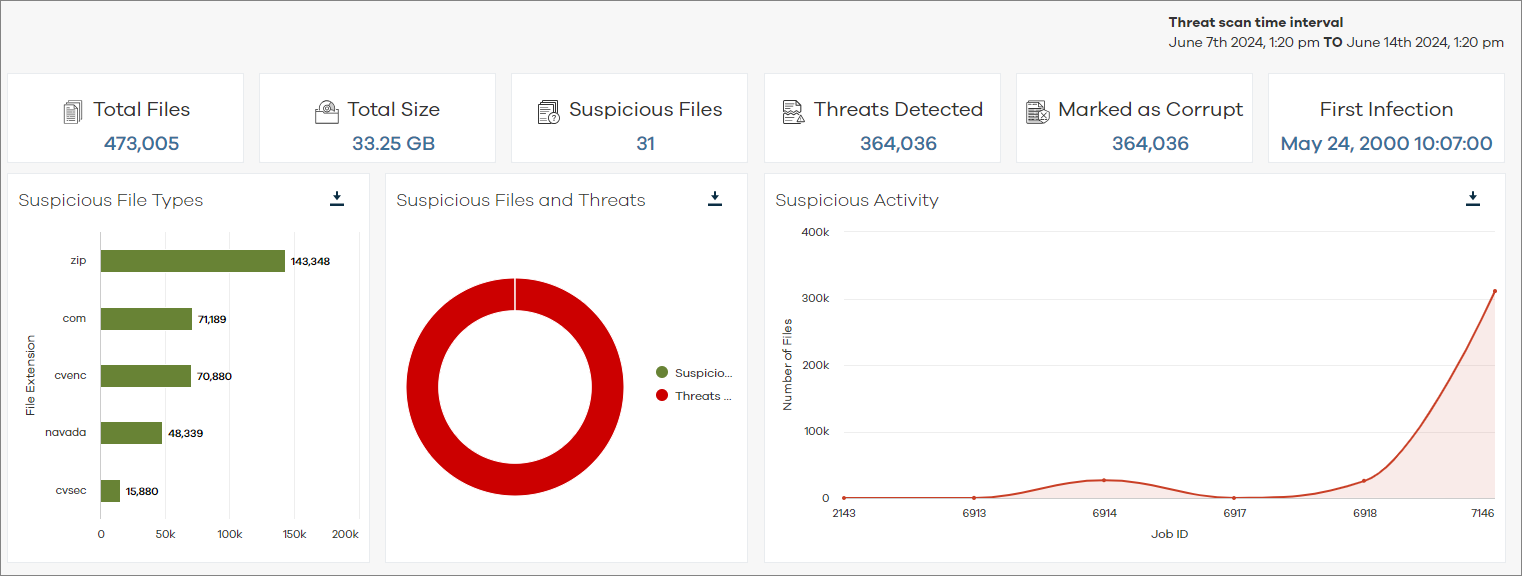
To re-populate the charts, you can click chart segments in the Suspicious File Types chart and Suspicious Files and Threats chart, and you can click Job IDs in the Suspicious Activity chart.
File Information Table
The File Information table is comprised of detailed information about the affected files in the client computer.
The following image is an example of the File Information table:
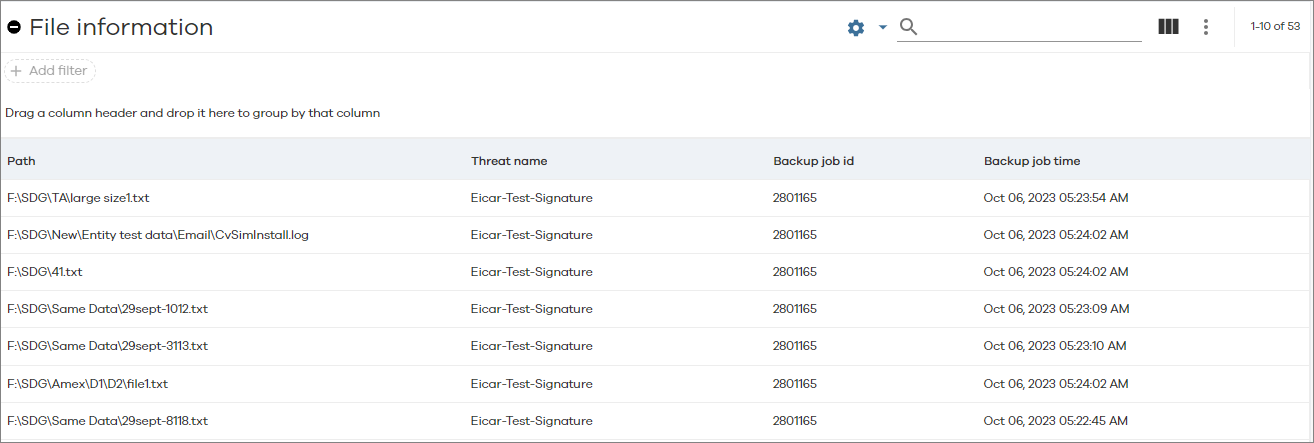
The following table includes descriptions for all columns in the File Information table for Threat Analysis.
|
Column |
Description |
|---|---|
|
Path |
The path to the folder that contains the backed up file. |
|
Threat name |
The name of the threat. |
|
Backup job id |
The ID of the backup job that backed up that file. |
|
Backup job time |
The time at which the backup was performed. |