You can configure STS role authentication using a tenant account ARN.
Procedure
-
Log on to the AWS console, using the admin account.
-
Create an IAM role to assume a role in a given account:
-
Create the role.
For example, create a role called vsa_assume_role.
-
To the role, attach a policy that has the sts:AssumeRole permissions.
-
Assign the role to the Amazon EC2 access node.
-
-
From the tenant account, create another IAM role to define a set of permissions for making AWS service requests:
-
Create the role.
For example, create a role called vsa_role.
-
Attach the policy that is required for backups and restores.
-
-
Download the amazon_restricted_role_permissions.json file, and attach it to the policy that is required for backups and restores.
-
To the role that you created in step 3, add the admin account ID as a trusted entity.
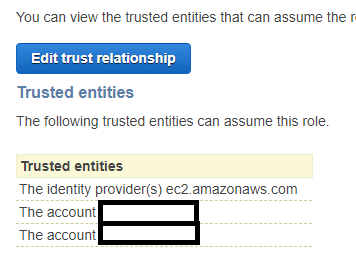
What to Do Next
When you create an Amazon hypervisor, specify the tenant account role ARN for the role that you created created in step 3 above (for example, vsa_role).
Related Topics
-
For more information about assigning AWS user permissions by creating a policy, see Overview of IAM Policies on the AWS documentation site.
-
For more information about editing trust relationships, see Modifying a Role Trust Policy Modifying a Role Trust Policy on the AWS documentation site.