You can map attributes in the identity provider (IdP) response to user attributes used in the Commvault software. For example, by default, a user email address is expected in the NameID element in the IdP response. If your IdP sends the user email address in an attribute instead of in the NameID element, you can map that attribute name carrying the value of email to user attribute (for example, Email) so that the value of the attribute is used for the user email address.
Available Attributes
You can map IdP response attributes to the user attributes in the following table. Your mappings take precedence over default sources.
|
User Attribute |
Details |
|---|---|
|
user name |
The mapping for the user name attribute is used to validate the user when they log on. The default source for the user name attribute is the NameID element. |
|
user groups |
The mapping for the user groups attribute is used to associate or disassociate the user with domain groups (external groups) that were added to the Commvault environment. |
|
|
The mapping for the email attribute is used to validate the user when they log on. The default source for the email attribute is the NameID element. |
|
user GUID |
If the Auto create user option is selected, the mapping for the user GUID attribute is used as the user GUID. If the Auto create user option is selected and a mapping is not provided, the user GUID is a system-generated value. |
|
SID |
Applies to: Active Directory identity providers The mappings for the SID attribute and the group SID attribute are used to facilitate the ACL (Access Control List) browse for agents such as the Windows File System Agent and the SharePoint Server Agent. |
|
Group SID |
|
|
company name |
Applies to: Multi-tenant Commvault environments The mapping for the company name attribute is used to configure SAML authentication at the CommCell level. The SAML authentication applies to all companies in the Commvault environment. For instructions about configuring SAML authentication at the CommCell level, see Configuring SAML Authentication for All Tenants . |
Procedure
-
From the navigation pane, go to Manage > Security > Identity server.
The Identity servers page appears.
-
In the Application name column, click the application name.
The application details page appears.
-
Under Attribute mappings, click Edit.
The Edit attributes dialog box appears.
-
Click Add mappings.
-
Enter the attribute name based on the format in the IdP response:
-
To add the attribute name in the URL format (for example, http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress), in the SAML attribute box, add the URL.
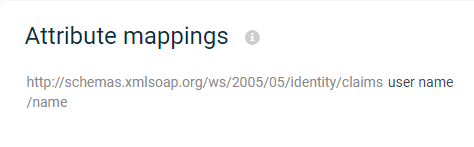
-
To add the attribute name in the generic name format (for example, uname), in the SAML attribute box, enter the name
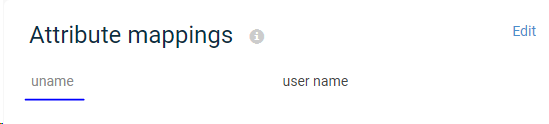
-
-
From the User attributes list, select the user attribute that the IdP response attribute maps to.
For example, if the IdP response attribute is http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress, click Email.
-
To add additional mappings, click Add mappings.
Note
If you add a user name mapping, you must add an email mapping too.
-
Click Save.
Examples
The following samples are mappings and the results of the mappings:
|
SAML Attribute |
User Attribute |
Attribute statement |
Result |
|---|---|---|---|
|
Generic format: uname URL format: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name |
user name |
Attribute in generic format: Attribute in URL format: |
The value jdoe is used to validate the user. |
|
Generic format: mail URL format: http://schemas.microsoft.com/2012/12/certificatecontext/field/subject |
|
Attribute in generic format: Attribute in URL format: |
The value jknight is used to validate the user. |
|
Generic format: usergroup URL format: http://schemas.xmlsoap.org/claims/Group |
user groups |
Attribute in generic format: Attribute in URL format: |
The user is associated with the Domain Users group. |
|
Generic format: company URL format: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/organization |
company name |
Attribute in generic format: Attribute in URL format: |
MyCompany is identified as a valid company in the Commvault environment, and the user is allowed to log on and view MyCompany information. |
Related Topics
For instructions about configuring SAML authentication at the CommCell level, see Configuring SAML Authentication for All Tenants .