The File extension tab in the Threat Indicators dashboard lists Windows file system clients with file extension anomalies.
Clicking a client computer opens the File Extension Report, which allows you to analyze the statistics for that client.
The File Extension Report displays information related to the possible presence of ransomware. The system monitors Windows file system backup jobs to detect if files have been encrypted. Ransomware can sometimes change the extensions of those files after encryption (for example, .ecc, .ezz, .zzz, .xyz, .abc, .ccc, .micro, .encrypted, etc.).
As part of Windows file system backups, the system scans for information on these file types (under the subclient content in the default backupset) to establish a baseline. Once the baseline has been established, subsequent incremental jobs continue to scan for information on these file types and identify potential file renames. The system then runs machine learning algorithms on the observed datapoints to identify if there has been abnormal activity resulting in a large number of file renames.
File Extension Tab
The table in the File extension tab is comprised of the following columns:
|
Column |
Description |
|---|---|
|
Name |
The client computer. When you click the client computer, the File Extension Report appears (see below), which allows you to analyze the statistics for that client. |
|
Indicators |
File extension |
|
Detected time |
The time when the anomaly was detected. |
|
Server type |
File system. |
|
File Count |
Number of files detected with the anomaly. |
|
Tags |
Audit tags that you can use to record actions. |
|
Actions |
Click the action button
|
Report Description
Click a client name in the File Extension tab to open the File Extension Report.
The File Extension Report is divided into the following sections: File Extension Trend chart and Suspicious Files table.
File Extension Trend
This chart displays information about the number of files and their file extensions that were backed up per backup job.
The following image is an example of the File Extension Trend chart for file extension anomalies:
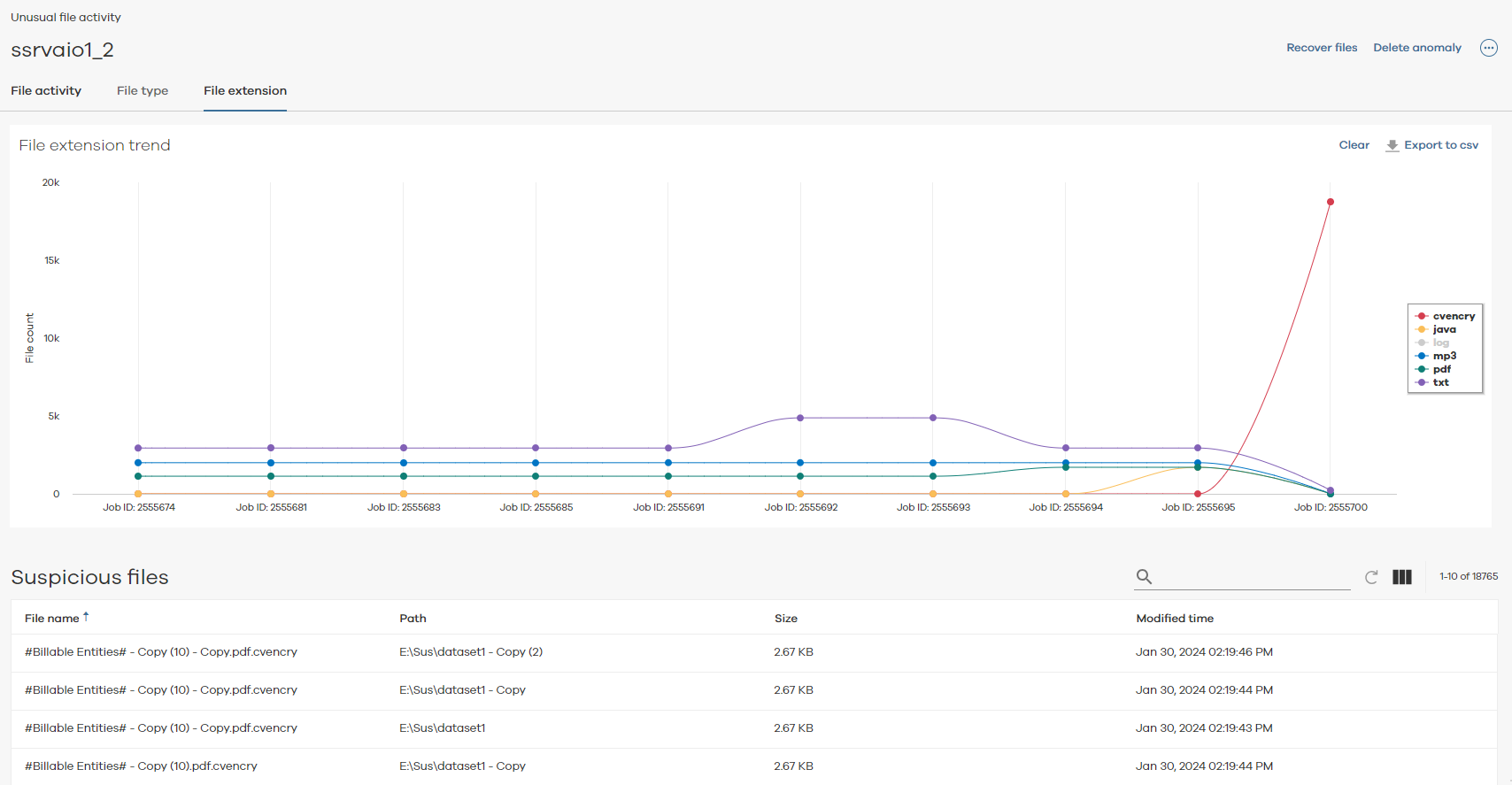
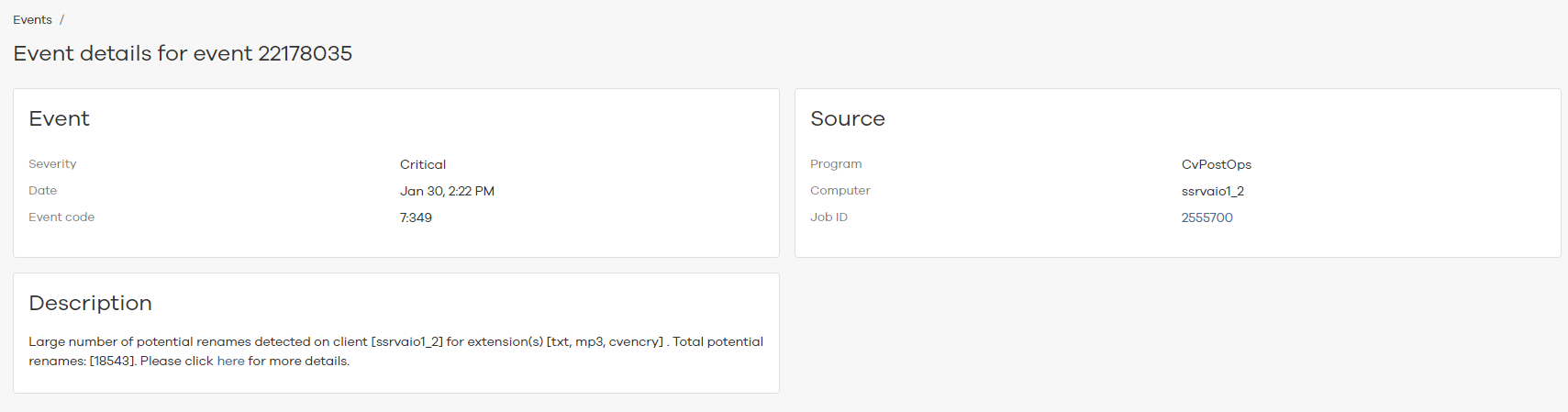
Click a node on the chart to open the event details for the backup job. The following image is an example of the event details for a job:
Suspicious Files Table
The following table includes descriptions for all columns in the Suspicious files table.
|
Column |
Description |
|---|---|
|
File name |
The name of the suspicious file. |
|
Path |
The file path of the suspicious file. |
|
Size |
The size of the susicious file. |
|
Modified time |
The time when the suspicious file was modified. |
 , and then select one of the following options:
, and then select one of the following options: