Cloud Assembly allows you to select and assemble all of the resources intended to be protected and recovered.
GCP Cloud Assembly Creation
To create a new GCP Cloud Assembly in Cloud Rewind, complete the steps shown below.
General Information
-
Enter the Cloud Assembly name and description.
-
Select the cloud connection for which the resources have to be protected.
-
Select the primary region from where the resources are to be recovered.
-
To protect cross-projects, do the following:
-
Move the Allow cross project protection toggle key to the right.
-
Select cross cloud connection for the destination GCP project.
-
-
Under the Advanced section, do the following:
-
To stop protecting resources locally, move the Keep local protection active toggle key to the left. By default, GCP resources are protected locally and across projects.
-
In Snapshot Protection Type, the option to select Multi-Regional or Regional protection is available.
-
By default, Multi-Regional protection will be selected. If you choose to store your snapshots in the selected regions only and not globally, then choose Regional protection.
Multi-Regional
Google Cloud uses the default location, which stores the snapshots in a Cloud Storage multi-regional location closest to the region of the source disk.
For example: If us-central1-a is the source disk, then the snapshot will be created in the US multi-region location.
Note: Only one snapshot will be created in the multi-regional location.
Regional
Select Regional option to choose a maximum of 2 recovery regions (selected during Cloud Connection creation), to create a timeline in the chosen regions.
Note: Extra costs might be incurred if you choose more than one region. Snapshot will be created in all the selected regions.
-
Resources
-
Select the resources that need to be protected based on Selected Resources or using the labels.
-
Selection using Labels can be made by matching all labels or matching at least label.
-
If you want to exclude resources from protection or manage exclusion of unprotected disks during recovery, move the Exclude resources with following labels toggle key to the right, add the labels to exclude resources that match the specified label.
For information about how to exclude GCP resources, see Excluding GCP Resources With Labels from Protection and Recovery.
Protection Policy
-
Select a protection policy to protect the resources.
-
Protection policy can be used to define the time at which the snapshot has to be taken and the number of snapshots to be retained using a retention count.
-
A policy template can be created to fit the protection needs best.
-
To learn more about creating a new protection policy template, click here.
-
The policy can be activated as by the scheduled policy, immediately triggering one policy or by delaying to the specific time.
Review
-
Review the general information, resource information, and the protection policy details provided.
-
Edit the details if required and proceed to finish and create a Cloud Assembly.
Actions
Once a GCP Cloud Assembly is created, you can find the following actions in the upper right corner:
-
Edit: In the Cloud Assembly Edit section, users can modify the cloud assembly's name and description under General Information. Additionally, users can update the recovery region and enable cross-account functionality as required. They can also adjust resource protection options and the protection strategy under the Resources and Protection Strategy sections, respectively.
-
Disable: The Disable option allows users to temporarily disable cloud assembly protection, which can be re-enabled as needed.
-
Configuration:
-
In the webhook section, users can set up custom automation scripts using the webhook options. Webhooks are HTTP/HTTPS callbacks that can be triggered pre- or post-recovery or post-reset. Click here to learn more about webhooks.
-
In the Recovery options sections, users have the ability to map shared VPC network recovery option.
-
-
Recovery Profile: Users can create different recovery profiles with associated webhooks for various recovery scenarios. This functionality streamlines the selection of webhook recovery templates based on specific needs.
-
Config Drift: This option effortlessly compares two or more protection timelines, enabling users to identify configuration differences between them.
-
Delete: The Delete option permits users to permanently remove the cloud assembly from the system.
Ad Hoc Backups
Cloud Rewind offers ad hoc backup capability for GCP, enabling users to trigger an immediate protection action outside of the scheduled backup cycle. Ad hoc backup provides flexibility by enabling immediate, policy-driven protection for GCP workloads, ensuring that business-critical workloads can be protected instantly when required. This feature allows enterprises to safeguard workloads while maintaining governance and consistency across multiple cloud environments.
Key benefits:
-
On-demand backups complement scheduled protection.
-
Policy-based retention ensures consistency.
-
Concurrency checks prevent conflicts with in-progress protection jobs.
Ad hoc backup is available through the following:
-
Cloud Assembly Actions (initiate backup directly on a selected assembly).
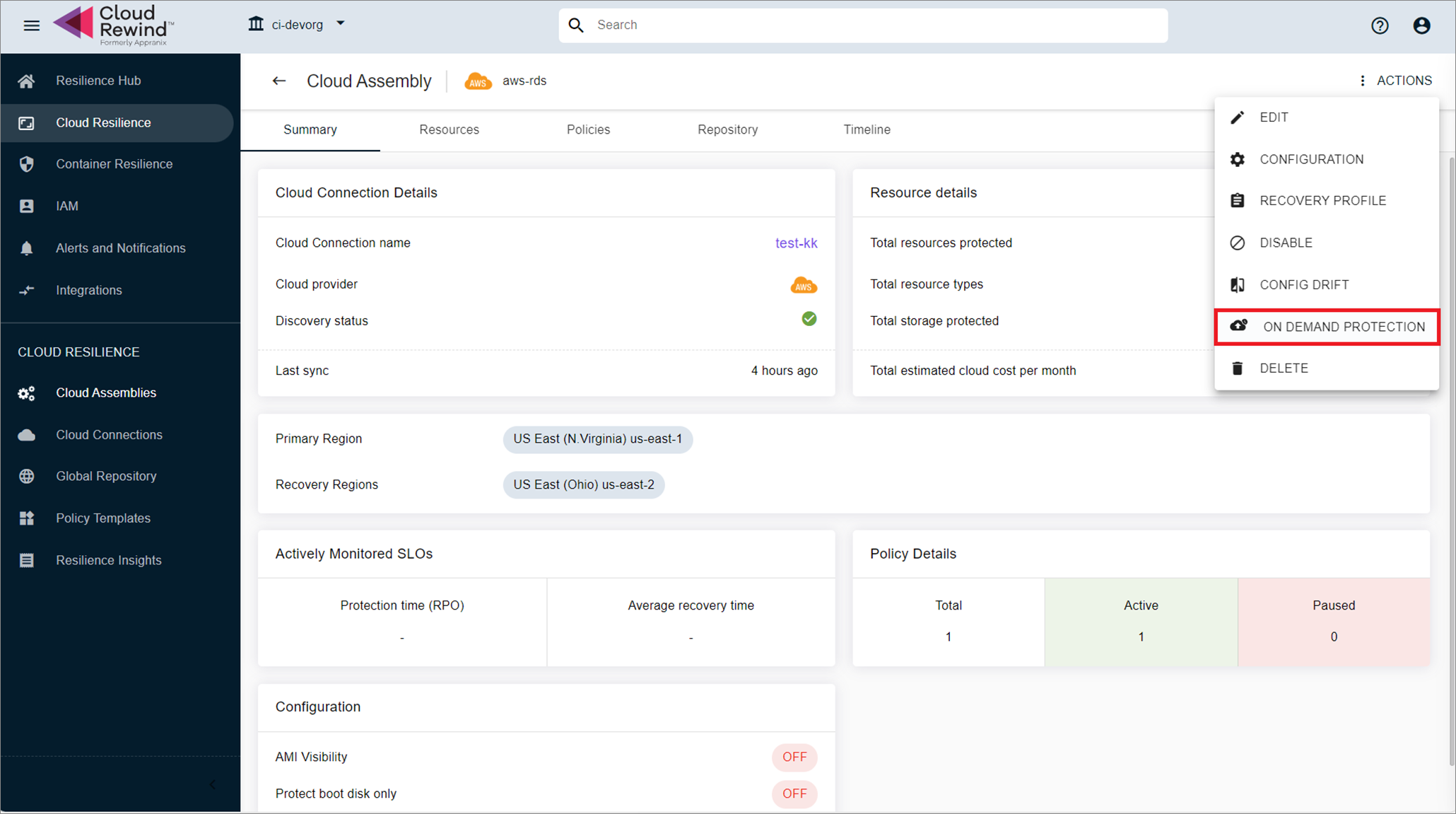
-
Protection Policy Actions (trigger backup based on an existing policy attached to the assembly).
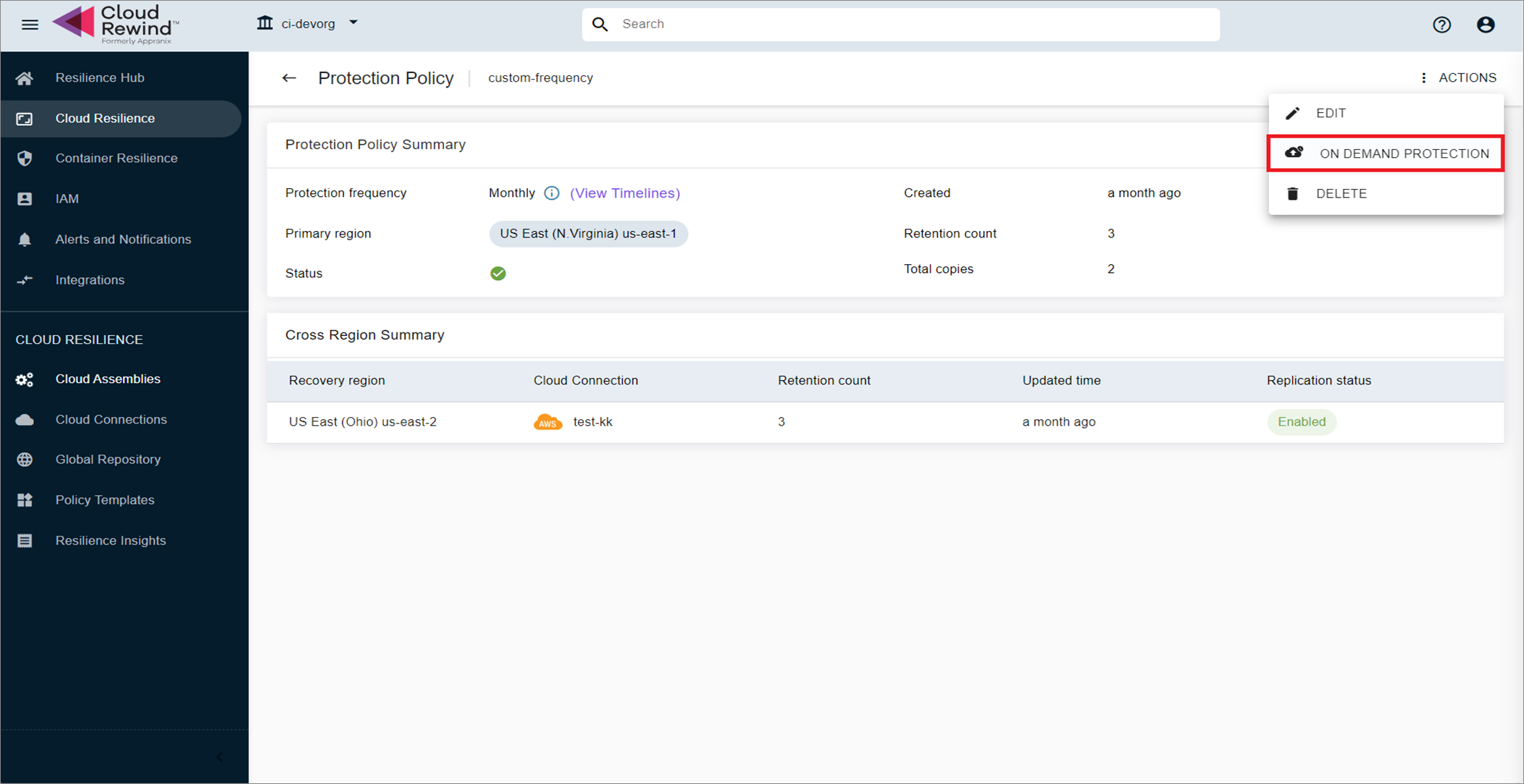
How Ad Hoc Backup Works
-
Policy Selection
-
If multiple protection policies exist for a Cloud Assembly, the user must select the appropriate policy to initiate the ad hoc backup.
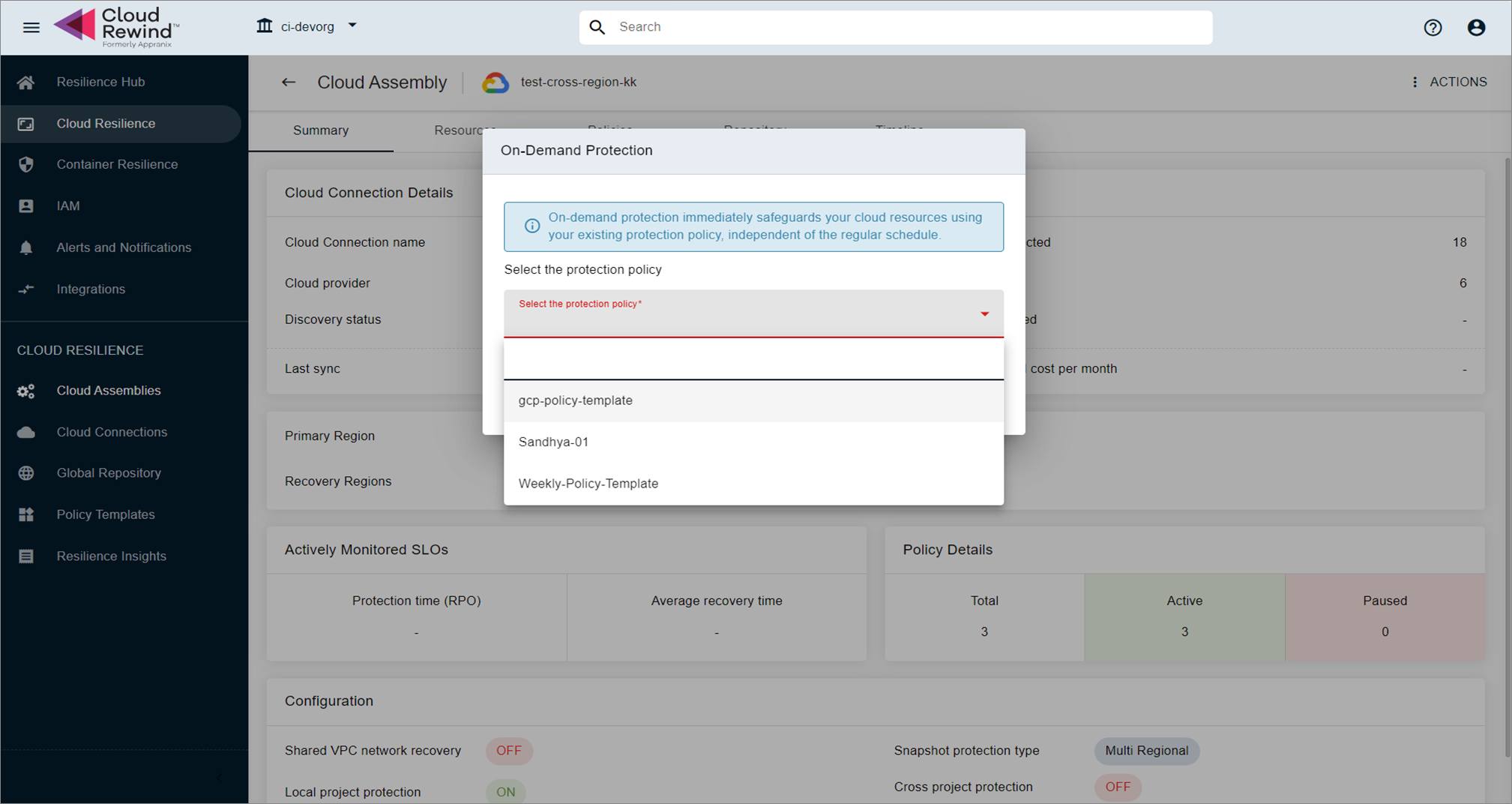
-
The backup will follow the retention rules of the selected policy (retention count applied as per policy configuration).
-
-
Execution
-
Once triggered, an ad hoc backup behaves like a scheduled protection job, creating a recovery point consistent with the selected policy.
-
The backup is logged and tracked in the Cloud Rewind job execution history.
-
Constraints and Limitations
-
Concurrency Restriction:
- If a scheduled backup or an ad hoc backup job currently is in progress for the same protection policy, an ad hoc backup cannot be triggered.
-
Policy Dependency:
-
An ad hoc backup requires an existing protection policy.
-
An ad hoc backup cannot be initiated without selecting a valid policy.
-
-
Retention Enforcement:
- An ad hoc backup is subject to the retention count defined in the selected policy. Older backups will be pruned according to standard policy retention rules.